Evolution of ICS and emerging challenges
This article explores the challenges and evolution in ICS security, highlighting the shift from isolated systems to interconnected networks vulnerable to sophisticated cyber threats. It underscores the necessity of robust cybersecurity measures, discusses the impact of major cyber incidents, and introduces strategic frameworks and controls aimed at enhancing the resilience of these essential systems.
Securing and supporting Industrial Control Systems (ICS) has been a challenge for a long time and for many organizations. In the early days of ICS technology, components like Programmable Logic Controllers (PLC), sensors, and devices were blissfully unaware of IT infrastructure and ran on proprietary networks and “busses” like Profibus or Modbus or Genius Bus or DeviceNet and ControlNet (FactoryTalk) from suppliers like Siemens, GE, Rockwell and others. Much of the logic was contained in the PLC and early terminal type factory management systems like Dextralog emerged in the 1970s.
In the 1980s, the explosion of the PC and MicroServer market was a tipping point. It led to a major change in ICS with a move to PC-based Human Machine Interfaces (HMIs), and server-based Supervisory Control and Data Acquisition (SCADA) systems, and subsequently Manufacturing Execution Systems (MES) which became part of the 4th industrial revolution.
The PLC of course got more CPU, and ethernet gateways were added to the bus technology, nevertheless the humble PLC still just followed its basic instruction set without transaction authentication (not to be confused with local PLC login). We unknowingly walked ourselves into a perfect storm, not unlike the epidemics humankind saw as man colonized the world, so what were physical and logical natural borders or breakpoints for IT and OT in the early days, now no longer protected us. Remember also the OT lifecycle was more than twenty years, IT is five to seven years at most, so change was inevitable.
Technological shifts and security implications
Operational Technology was being controlled by IT Technology, and upstream ERP systems drove factory planning and recipe information, and financial controllers, markets, operations, and a myriad of others wanted to visualize and consume data from these OT systems. Along came wireless handheld devices like Radio Data Terminals, and even industrial tablets, so the OT environment had become mobile as well.
While all of this was happening, manufacturers of these automation systems were extremely slow to certify their product on newer technologies as open source and commercial operating systems rapidly advanced on both full and delta release cycles. Users or consumers of the technology found themselves dealing with conflicting objectives; their systems were validated by regulators and licensed, thus making any change nearly impossible without re-validation. Manufacturers simply failed to keep up and certify their products on delta or new releases of the platform families they supported. Not surprisingly IT and OT support staff had to manage this dilemma, which pretty much meant that vulnerabilities went unpatched, and more and more relied on the fragile control of “air gaps,” ie., the physical separation, between the Enterprise and OT. It was idealistic but, in truth, a fallacy. The challenges were not just product integrity and critical control points, but safety systems as well. The first and most famous state-sponsored attack, Stuxnet, destroyed numerous centrifuges in Iran's Natanz uranium enrichment facility by causing them to burn themselves out by defeating centrifuge maximum RPM thresholds.
While turnstiles and swipe cards initially served as effective physical barriers to secure sensitive areas, the rapid evolution of technology has complicated their efficacy. The sophistication of integrated systems, especially with the rise of the Internet of Things (IoT), now generates vast quantities of real-time data. This complexity, paired with the logistical and financial impracticalities of on-site support—where waiting for an engineer to travel internationally for diagnostics and repairs is no longer viable—has pushed many organizations to adopt more agile, cloud-based solutions. Additionally, as Enterprise Resource Planning (ERP) systems migrated to the cloud and mobile devices began delivering personalized, real-time data, traditional physical security measures became inadequate. These developments led to a natural but critical shift in how organizations approach the security of their operational technologies.
As industrial systems became increasingly digitized, the traditional physical separation between Information Technology (IT) and Operational Technology (OT) networks—known as the air gap—transformed into a virtual concept. Advanced network technologies such as Virtual Local Area Networks (VLANs), Virtual Routing and Forwarding (VRF), and firewalls were implemented to create segmented and controlled network access. Additionally, Privilege Access Management tools utilizing jump box technology, alongside APIs, middleware, and message brokers like MQ, were integrated to enhance security protocols. However, these measures also coincided with increased risks from insiders equipped with portable devices like smartphones, tablets, and wearables featuring connectivity options such as Wi-Fi, Bluetooth, and NFC—all requiring USB connections for charging. This blend of convenience and connectivity presented new vulnerabilities, complicating the security landscape significantly.

Control assessments are not just a compliance exercise
Cyber risk quantification can help you make informed decisions on the prioritization of controls.
Modern threats and response
The impact of cyber threats on industrial systems has been both dramatic and devastating. High-profile malware and ransomware attacks such as Stuxnet, Eternal Blue, Petya, NotPetya, and WannaCry illustrate this new reality.
While not all of these cyber threats manage to breach the divide between enterprise IT environments and operational technology (OT) systems, the consequences are uniformly severe—ranging from denial of service to complete operational shutdowns, leading to significant financial losses. These incidents are well-documented, with major corporations facing staggering financial repercussions: pharmaceutical giant Merck suffered an $870 million loss; FedEx reported a $400 million setback; French construction firm Saint-Gobain experienced a $384 million loss; Danish shipping company Maersk took a $300 million hit; snack company Mondelēz faced a $188 million loss; and British manufacturer Reckitt Benckiser reported a $129 million loss.
These figures are not just abstract numbers but stark reminders of the tangible impact of cyber threats. Beyond commercial losses, critical infrastructure sectors including healthcare, power generation, and gas distribution have also been significantly disrupted globally, underlining the pervasive risk these threats pose to both economic stability and public safety.
The challenges posed by cyber threats to industrial control systems are not only well-documented but are continually evolving, impacting globally recognized brands and critical infrastructure alike. In response, leading authorities on cybersecurity have developed and refined various control frameworks to guide organizations in fortifying their defenses. Noteworthy among these are NIST SP 800-82 for industrial control system security, ENISA's guidelines on Industrial Control System Protection, and the ISO 15745 family of standards focused on integration of networked industrial devices.
Recently, the SANS Institute contributed to this body of knowledge with the publication of "The Five ICS Cybersecurity Critical Controls," a set of foundational security measures specifically tailored for the needs of ICS environments. These controls are designed to prioritize actions that significantly reduce risk and enhance response capabilities:
Control No. 1: ICS-specific Incident Response Plan
A bespoke incident response strategy that addresses the unique operational and safety challenges posed by ICS environments.
Control No. 2: Defensible Architecture
The creation of a network architecture that inherently limits the spread of breaches and enables effective containment of threats.
Control No. 3: ICS Network Visibility and Monitoring
Implementing tools and practices that provide real-time insights into network activity to detect and respond to potential threats swiftly.
Control No. 4: Secure Remote Access
Establishing secure and controlled remote access solutions to ensure safety and integrity of system operations when accessed from outside the network.
Control No. 5: Risk-based Vulnerability Management Program
A proactive approach to managing vulnerabilities that prioritizes risks based on their potential impact on the ICS environment.
These controls represent a strategic framework to guide organizations in strengthening their cybersecurity posture against a landscape of persistent and evolving threats.
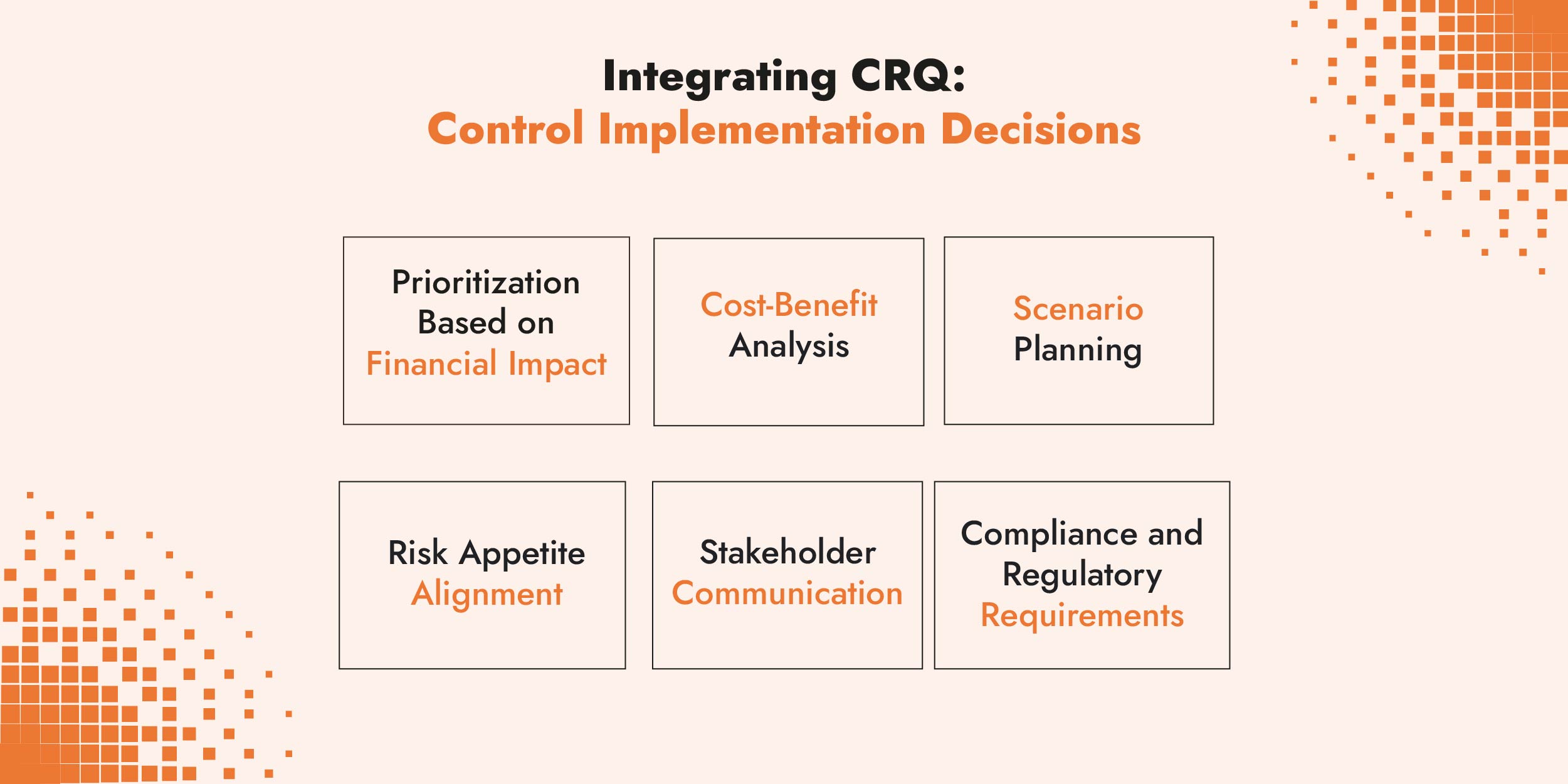
Cyber quantification and managing risk
In addition to the critical controls Cyber Risk Quantification offers a methodology to establish a financial cost for risk scenarios and provides more powerful rationale over qualitative methods for decision makers when investing in controls.
A quantitative approach allows organizations to make informed, data-driven decisions about which cybersecurity controls to implement by providing a clear financial analysis of risk scenarios.
C-Risk cybersecurity and risk management experts use the Open FAIRTM Risk Analysis (O-RA) Standard and the Risk Taxonomy (O-RT) Standard. Using the FAIR framework, it is possible to map quantified risk scenarios to control frameworks to establish meaningful financial thresholds for risk-based decisions on the SANS ICS control domains as well as other control frameworks.
If you would like to learn more, schedule a call with a C-Risk expert.

We build scalable solutions to quantify cyber risk in financial terms so organizations can make informed decisions to improve governance and resilience.








